Overview
BattlEye is a German anti-cheat developed by Bastian Heiko Suter. It offers game publishers easily integrated anti-cheat solutions, using the newest mechanisms and game-specific detections to provide the best security. BattlEye consists of multiple organs that work together to catch and prevent cheaters. The anti-cheat is packed and virtualized using VMProtect.
The four main pieces of BattlEye are:
- BEService
- Windows NT-Service that communicates with BEDaisy, which reports detections through a named-pipe to the BEClient.
- BEDaisy
- Windows kernel driver that uses callbacks and minifilters to prevent cheater from touching the memory.
- BEClient
- Windows dynamic link libary that contains the most detection routines. It is mostly injected after game initialization.
- BEServer
- Backend-server owned by the game publisher used to collect information and take actions against cheaters.
BattlEye initialization
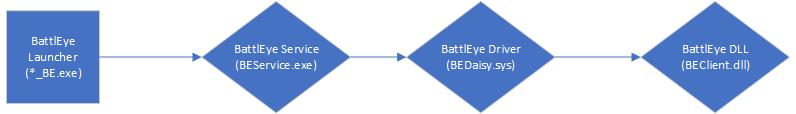
Behind the scenes
At first, the BattlEye launcher registers the windows NT-Service “BEService” and starts it. When the service has been started, the launcher will connect to the named pipe “\.\pipe\BattlEye” created by the service. The pipe will be used to transfer information between the launcher and service. All packets sent through the pipe are unencrypted:
- The first packet reads information from the configuration file (BELauncher.ini) and sends information to verificate the session. It contains the following data:
- Packet-ID (0) Game-ID BasePort (configuration file) ProcessId (of the launcher) Game Executable Name (e.g. Unturned.exe) Service Path Ths second packet is 4 bytes long and only contains the process-id of the game after it has been started. Once the launcher has sent the first packet, the windows service will create and start the kernel component “BEDaisy.sys”. The kernel driver installs callbacks and minifilter and reports the status back to the service. The connection between the service and kernel driver is encrypted using a custom XOR algorithm.
- After the driver did its job, the service will contact the launcher to start the protected game and load the usermode module “BEClient.dll”
Once the launcher has sent the first packet, the windows service will create and start the kernel component “BEDaisy.sys”. The kernel driver installs callbacks and minifilter and reports the status back to the service. The connection between the service and kernel driver is encrypted using a custom XOR algorithm.
After the driver did its job, the service will contact the launcher to start the protected game and load the usermode module “BEClient.dll”
BattlEye detections
- BEService
- Detects blacklisted drivers using CreateFileA (blackbone)
- Detects blacklisted signatures, received from BEClient in every process
- Detects blacklisted code signing certificates
- BEClient
- Detects abnormal memory pages
- Detects blacklisted processes/modules/windows
- Detects memory changes (.text section)
- Detects modifications of lsass and steam game overlay
- Detects thread modifications using timing checks (Sleep)
- Detects public bypass known as NoEye
- BEDaisy
- Detects thread, process and image creation
- Detects module sections (minifilter)
- Detects blacklisted driver (cheat engine DBK)
- Detects opened process and thread handles through ObRegisterCallBacks