Overview
EasyAntiCheat is an anti-cheat owned by Epic Games. It protects games through the use of hybrid anti-cheat mechanisms. EasyAntiCheat is made of multiple modules that work together to avoid cheater. The anti-cheat is packed and virtualized using VMProtect.
The main modules of EAC are:
- Launcher application (mostly called EACLauncher.exe)
- Windows application that downloads the newest EAC modules and processes the launch of the game using the launcher module.
- Launcher module
- Windows dynamic link library that gets mapped into the launcher application to communicate with the driver.
- EasyAntiCheat.exe
- Windows NT-Service that controls the kernel mode driver. It starts and stops the driver according to the game status.
- EasyAntiCheat.sys
- Windows kernel driver that uses callbacks and minifilters to prevent access to the game.
- Game module
- Windows dynamic link library that gets mapped into the game application to initialize the main scan routines in usermode.
- Dummy process (dllhost.exe)
- Windows NT-Service that gets abused to scan for blacklisted code signing certificates.
File encryption
When analyzing the windows NT-Service (EasyAntiCheat.sys) you may notice that EAC utilize a simple arithmetic method to decrypt the modules received from the server. The launcher module downloads the newest driver into the following path:
%appdata%\EasyAntiCheat{gameid}\easyanticheat_wow64.eac
It looks like the following when opening the file in any hex editor:
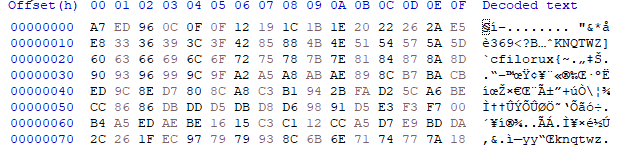

The service opens global named shared memory in order to receive the newest version from the server. The section gets written by the launcher module when injected:
The file is encrypted in the .data section of the launcher module.
Kernel mode driver
As mentioned above, the driver makes use of the kernel mode callbacks to protect the game. EasyAntiCheat has different input/output control codes (IOCTL) which are used for initialization:
- 0x226003 – Used to retrieve the driver version (Current version is 0x35).
- 0x22E007 – Used to transfer the encrypted game module and to provide the basic information to process further.
- 0x22E01F – Used to check specific usermode functions of ntdll (NtCreateUserProcess, NtAllocateVirtualMemory, NtWow64WriteVirtualMemory64, NtWow64AllocateVirtualMemory64, NtWriteVirtualMemory) The interesting code is 0x22E007. The launcher module provides basic information in order to protect the main game:
1
2
3
4
5
6
7
8
9
10
11
12
typedef struct __declspec(align(1)) _eac_22E007
{
char pad_0x0000[0x8]; //0x0000
ULONG SyncEvent; //0x0008
ULONG UMCallback; //0x000C, Usermode-Callback
char pad_0x0010[0xC]; //0x0010
__int32 ThreadId; //0x001C
__int32 GameId; //0x0020
char szProcessName[256]; //0x676888
ULONG FileDataSize; //0x0124
CHAR FileData[]; //0x0128
} eac_22E007;
The structure will be transfered encrypted using the device handle “EasyAntiCheat”. The encryption used here is a XTEA (extended Tea) implementation:

The key used for the en- and decryption is built using the actual buffer address and the process id:
1
2
3
4
5
ULONG key[4];
key[0] = p_InBuffer; // (Address of InBuffer in DeviceIoControl)
key[1] = 0;
key[2] = PsGetCurrentProcessId();
key[3] = 0;
The driver uses APC injection to map the file into the game process. The explanation for this method can be found here.
Detections
- EasyAntiCheat.sys
- Detects blacklisted kernel driver
- Detects attached debugger
- Detects kernel patches (ntoskrnl)
- Detects Xenos Injector
- Detects various kernel driver and exploits (WIN64Ast, VirtualBox Exploit, DBK64, WinDbg, HideToolz, PCHunter64, PowerTool X64, Moonlight Engine, LiveKD, Process Hacker, SMEP Bypass (C), CPU-Z, WinPmem, VirtualHardwares, Global Hack, WinD64, WinDivert, Iuebesks, Windows Kernel Explorer)
- Detects hidden processes
- Detects memory patches (.text)
- Detects blacklisted pooltags (TDL)
- Detects context changes (dr0, …)
- Detects opened handles (through the scan of the handle table)
- Detects blacklisted module (Dumper.dll, Glob.dll, mwsock.dll, perl512.dll, vmclientcore.dll, vmwareui.dll, virtualbox.dll, qtcorevbox4.dll, vboxvmm.dll, netredirect.dll)
- Detects system threads with a unmatched driver(threads started by manual-mapped driver)
- Game module
- Detects remote thread creations
- Detects memory patches (.text)
- Detects driver modifications
- Detects various hooks in different games.
More will be explained in the part 2.